"My Honeypot brings all the hackers to the yard!"

Table of Contents
-Introduction
-Platform/Technologies
-Time/Place
-Source of Attacks/Attack Map
-Analysis of Attacks
-Closing Thoughts/Conclusion
Introduction
For those reading this report and being saying "hey, that is not the title of the song", you're correct. The title of this report is a play on the song Milkshake by Kelis in 2003 (yes, I'm old) which had the ultra popular verse "My milkshake brings all the boys to the yard". I think the same can be said with a Honeypot. A Honeypot in its most basic sense, is a computer system that has been sacrificed as a way to attract cyberattacks, and be used sort of like a decoy. It mimics a target for hackers, and uses their intrusion attempts to gain information about cybercriminals and the way they are operating or to distract them from other targets that may be on your network. Honeypots are made attractive to attackers by building in deliberate security vulnerabilities. For example, a Honeypot can have open ports that can be susceptible to different kind of port scans or weak passwords. In this case, vulnerable ports were left open to entice attackers into the Honeypot environment. From there, that information can be used to see the time and source location, different types of services used, types of attacks, etc., all in a safe environment.
Platform/Technologies
In order to create the Honeypot environment, I used the vendor services of Amazon AWS. Through Amazon AWS, I was able to set up an EC2 instance (one of AWS's products) using a Debian 11 OS which provided the following tools and applications Adbhoney, Dionaea, and Honeytrap. These tools provided me with the necessary information to monitor and log the different malicious attacks that were taking place in my Honeypot. The Cowrie report was used to produce the information in this report and can be found within the Honeypot application.
Time/Place
May 18th, 2022 1300 - May 19th, 2022 1200
Northern California, USA
Source of Attacks/Attack Map
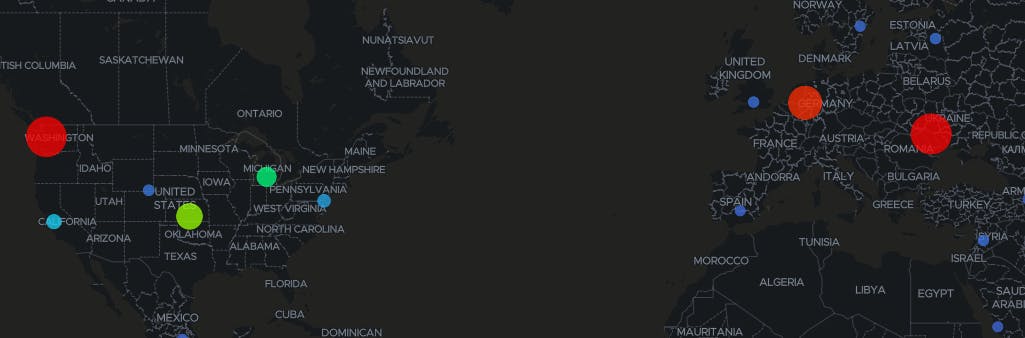
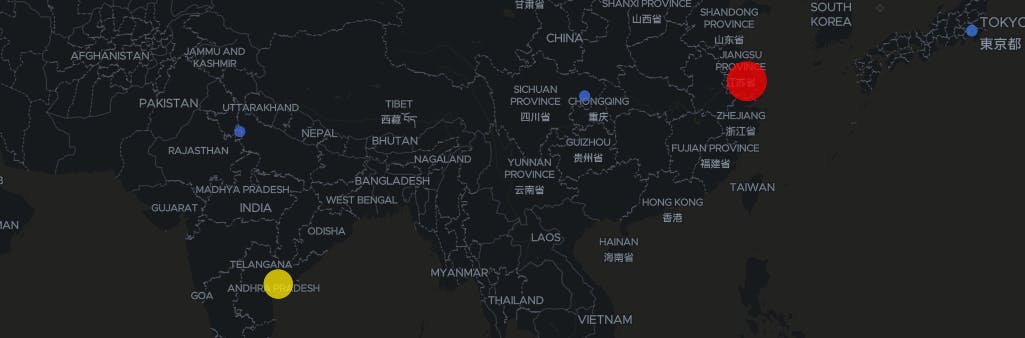
If you look on the two maps above, you will see where the different attacks were taking place. As a rule, the larger the circle, the more there is a concentration of attacks coming from that area. As you can see, the areas with the most concentrated attacks are Washington, USA/5,190 attacks, Germany/4,030 attacks, Moldova/5,264 attacks, India/3,257 attacks and Shanghai, China/5,092 attacks. Surprisingly enough, Moldova had the highest amount of attacks against our Honeypot even though it is on the list with countries with the infrastructure to be perceived as a stronger threat.
Analysis of Attacks
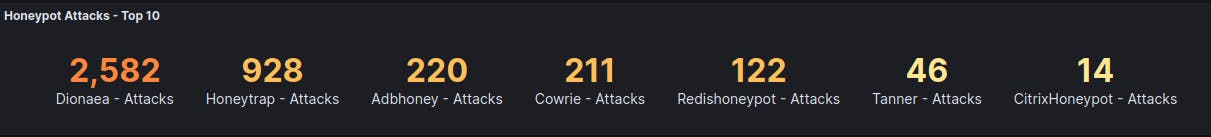
As you can see from our different Honeypots listed above, majority of the attacks were against my Dionaea and Honeytrap Honeypots. In order to understand why those two Honeypots were attack the most, we first have to know what each one is attracting. The Dionaea Honeypot is used to trap malware exploiting vulnerabilities exposed by services offered to a network. We use Dionaea to ultimately gain a copy of the malware in order to examine it further. My Honeytrap Honeypot is a low-interaction honeypot and network security tool which is used to catch attacks against TCP and UDP services.
When hackers are looking to gain unauthorized access to a device, server, etc., one of the more popular methods they use is called “Bruteforcing”. When a hacker is using bruteforce attack, they are attempting to gain access to a system utilizing a wide range of username and password combinations. Depending on how complex the account credentials are, this method may prove to be the easiest and quickest way inside. This is why it is not best practice to use easy passwords or to continually recycle passwords because they can pose a major threat to the user.
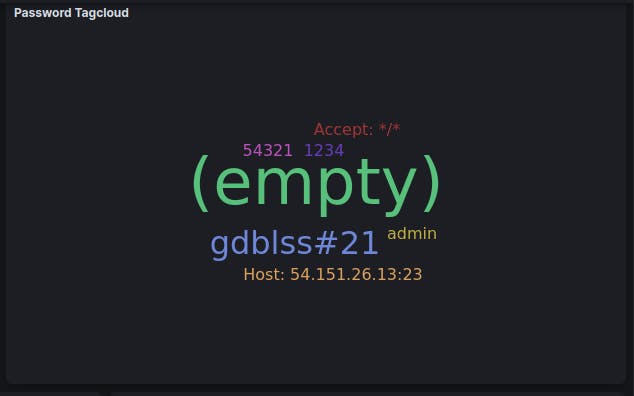
As you can see above, this shows the most common password attempts used by hackers in order to gain access. If it shows up in the photo, that means that is has been used before. The larger the font, the more times it has been attempted.
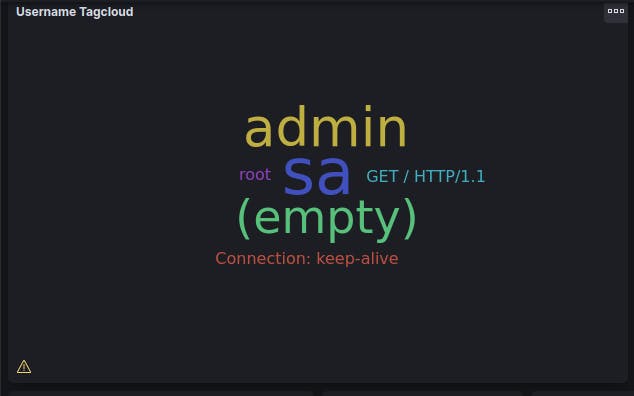
The same can be applied for the usernames up above. These are the most common usernames attempted by the hackers looking to gain access. The larger the font, the more times that is has been attempted. As you can see, there is not a whole lot of originality, but sometimes you don't need it. A lot of civilians leave access to certain programs or applications that require a password to default. So you can't really fault a hacker for starting there first.
Closing Thoughts/Conclusion

In closing, after close review of the Honeypot located in Northern California, USA, it is safe to say that there are a lot of attackers out there looking to take advantage of vulnerable servers, machines, etc,. After reviewing all of this data and seeing how this is just one server that received thousands of attacks for only being online for a little over a day, it shows that there is a significant need for cybersecurity professionals who are able to combat hackers. It also shows that outside of this country, there are plenty of countries or "nation states" who have the desire and know-how to attack hosts around the world, especially the United States. Therefore, it is incumbent on upcoming cybersecurity professionals to be well versed in methods and strategies needed in order to protect assets for both the government and private entities. I look forward to contributing in that effort and take my passion for cybersecurity and keep building and adding to my knowledge base, in order to be apart of the defense needed to keep our country safe from cyber attacks.
